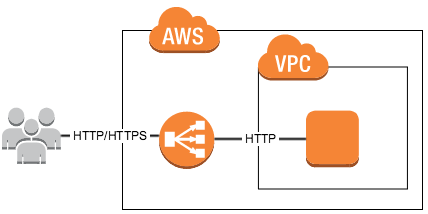
Your web server is running on port 80 to listen http connections on AWS Ec2 instnace. After that configured AWS ELB to listen on HTTP and HTTPS protocols and forwarding all the requests to backend server on port 80 only. The Amazon Elastic Load Balancer (ELB) supports X-Forwarded-Proto header value include the protocol of application.
Here we will use X-Forwarded-Proto header value of the HTTP request, and apply the rewrite rules if the client protocol is not HTTPS.
Below are the configurations for Apache, Nginx and IIS to force redirect to HTTPS behind AWS ELB.
APACHE
Make sure to enable rewrite module for apache. Edit the VirtualHost conf in a text editor and add following contents:
<VirtualHost *:80>
...
RewriteEngine On
RewriteCond %{HTTP:X-Forwarded-Proto} !https
RewriteRule ^.*$ https://%{SERVER_NAME}%{REQUEST_URI}
</VirtualHost>NGINX
Edit the HTTP server block in your domain’s configuration and add below contents:
server {
listen 80;
...
location / {
if ($http_x_forwarded_proto != 'https') {
rewrite ^ https://$host$request_uri? permanent;
}
}
}IIS
The windows servers with IIS web server edit the web.config file and add the following code under the section:
<rewrite>
<rules>
<rule name="Force Redirect to HTTPS" stopProcessing="true">
<match url="^(.*)$" ignoreCase="false" />
<conditions>
<add input="{HTTP_X_FORWARDED_PROTO}" pattern="^http$" ignoreCase="false" />
</conditions>
<action type="Redirect" redirectType="Found" url="https://{HTTP_HOST}{REQUEST_URI}" />
</rule>
</rules>
</rewrite>